Restrict Access to VM Applications by IP
Summary
For those that are unaware, a low-cost solution to hosting applications in Azure is to host them in Linux Ubuntu. I’ve been asked how to secure the apps at different levels. Here is a quick tip for securing applications inside a VM by restricting them to specific IP ranges.
This isn’t a production tip, it’s a good option when developing applications in Azure for rapid prototyping.
Default Settings
By default, all InBound traffic is restricted. There may be certain ports that you have opened up during the creation of the VM, port 80 (HTTP). In this instance, you can go to the PORT 80 rule and change the Source from Any to IP Addresses, then add the IP Address in.

Restrict Access to a Single IP
For a developer machine, if you want to enable all ports and access to a specific IP address, do the following:
Go to the Network Security Group of the VM, and add a new Inbound Security rule.
Select the Source, as Source IP addresses/CIDR ranges. Add the IP address you want to restrict to, followed by a range.
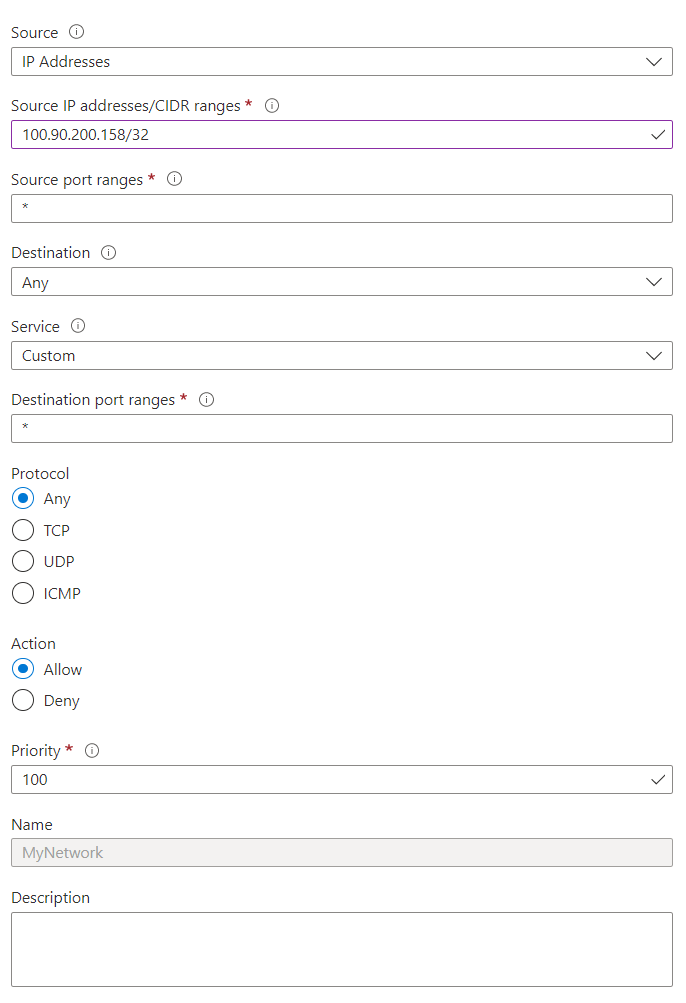
This will immediately block access to IPs outside of the IP entered.
